Hashicorp Boundary Enterprise Crack is a solution that offers the ability to create secure, granular access controls across your infrastructure, enabling Zero Trust networks. Using adaptive microperimeters, organizations can limit access to sensitive resources and data, prevent internal threats, and easily prove compliance.
What is Free download Hashicorp Boundary Enterprise Crack?
Hashicorp Boundary Enterprise Crack is designed to provide organizations with a simplified way to implement a Zero Trust security model and least privilege access across infrastructures. It establishes a framework for controlling authentication, authorization, and audits centrally from a unified management interface.
By authenticating users and workloads, enforcing granular access policies, and creating secure connections between resources, Boundary strengthens security postures and minimizes the risk of breaches. It integrates with existing identity and business systems to streamline deployment.
Key capabilities:
- Granular access control based on user or workload identity, attributes, and context
- Prevents lateral access between assets and isolates development environments
- Centralizes policy management and visibility of user sessions
- Just-in-time provisioning of user access
- Built to work with both legacy and modern apps, reducing friction
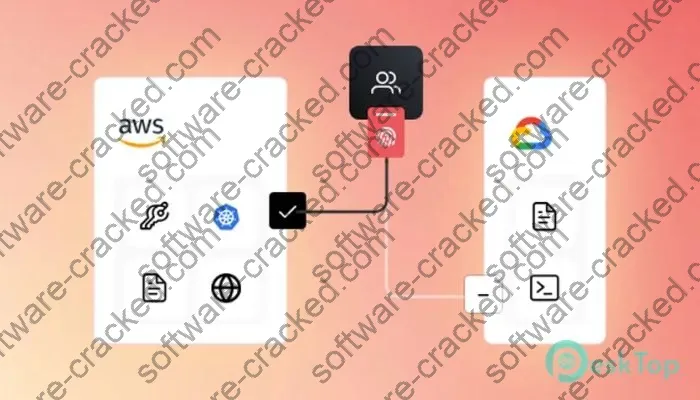
Boundary accomplishes this through a several components working together: * Boundary Controller: Orchestrates and manages the system, policies, connectors, and endpoints – installed on Linux or as a VM. * Boundary Connectors: Brokers secure access established between endpoints – available as a VM, container, or binary. * Boundary Identity Provider Integrations: Leverages existing systems like Ping, Okta, or LDAP for user authentication. * Boundary Enterprise Cloud: Handles administration, analytics, logging, and other services – hosted on AWS.
See also:
How Does Hashicorp Download free Hashicorp Boundary Enterprise Crack Work?
The underlying security framework behind Full version crack Hashicorp Boundary Enterprise Crack is enforcing Zero Trust principles and least privilege access using microperimeters.
Instead of just authenticating users or devices and implicitly trusting everything inside the network, access control decisions shift to be based on dynamic context like roles, attributes, location, time, and approved apps. These microperimeters provide granular segmentation that secures organizations against both external and internal threats.
Authentication and Authorization
Integrations with various identity providers via SAML or OIDC handle validating the identities of users. This uses existing company-wide systems like Active Directory or Okta to keep things streamlined under one access management system.
Authorization and access policies then codify which resources a given role requires – for example, limiting only the finance team to the accounting software. Conditions can be set based on specific user attributes, time of access, and method of access. Access expires automatically when conditions change.
Instead of blanket permitting or denying access, the rules become much more nuanced for exactly what is required. Boundary uses these parameters to determine who can reach which internal resources.
Establishing Secure Connections
Boundary establishes encrypted, mutually authenticated tunnels between resources that requests must traverse in order to access protected applications and infrastructure. All connections are brokered by Boundary connectors via the controller.
This has the effect of limiting lateral movement across networks even if access credentials are compromised. There are no implicit pathways. Assuming the identity of another user also does not enable unauthorized access due to identity-based policies.
Granular Access Controls
Because access is granted based on identity and context as opposed to network locations and static roles, administrators gain very tight control:
- Contextual access: Who is requesting access, what are they requesting, from where, using what device?
- Time-limited access: Short-lived credentials mean compromised ones expire quickly.
- Just-in-time (JIT) provisioning: No sittingunused service accounts. Users get temporary credentials just before use.
Centralized Administration and Monitoring
Hashicorp Boundary Enterprise Crack makes granting, modifying, and auditing access to internal resources easier to reason about from one place. The management UI offers:
- Overview dashboard showing identities, grants, trends, and alerts
- Graph database documenting relationship chains between users, policies, and resources
- Detailed activity logging for compliance and forensics review
- Usage analytics around access patterns
This visibility coupled with the identity-based segmentation makes responding to incidents and proving compliance requirements easier.
Implementing Download free Hashicorp Boundary Enterprise
A few key considerations when planning a Hashicorp Boundary Enterprise Free download rollout include preparing infrastructure, integrating existing systems, deployment architecture, and scaling:
System Requirements
Boundary can run on most modern Windows, Linux, and MacOS environments. This extends to supporting various cloud platforms as well. Minimum server requirements start at 2 CPU cores and 4GB of RAM.
Integration with Other Security Tools
In addition to identity providers, Boundary can integrate with SIEM, monitoring, incident response, and other security platforms via APIs.
Scaling Your Implementation
Additional Boundary connectors can be deployed to handle more load balancers, proxies, ingress controllers, and other access points that need to broker access to infrastructure through microperimeters.
As Boundary usage expands, the architecture can grow to span multiple regions and data centers. The controller consoles can be centrally managed with read replicas distributing configuration.
See also:
Quick N Easy Web Builder Activation key 11.0.0 Full Free Activated
This platform is absolutely amazing.
I appreciate the new layout.
It’s now far more intuitive to get done tasks and manage content.
The performance is so much faster compared to the previous update.
I absolutely enjoy the improved layout.
The latest enhancements in release the newest are incredibly awesome.
It’s now much more intuitive to do work and track content.
The performance is so much improved compared to the previous update.
I would strongly suggest this software to professionals wanting a robust product.
I love the improved layout.
It’s now a lot more intuitive to get done projects and organize data.
I appreciate the enhanced UI design.
It’s now far simpler to get done work and manage content.
I would definitely endorse this program to anybody looking for a robust platform.
The responsiveness is a lot improved compared to the previous update.
The loading times is significantly better compared to the previous update.
This tool is absolutely amazing.
The responsiveness is significantly better compared to the previous update.
The new functionalities in version the latest are really great.
This tool is definitely amazing.
I really like the improved layout.
I would strongly suggest this program to anyone looking for a powerful product.
I would strongly endorse this tool to anyone wanting a high-quality solution.
The recent functionalities in release the latest are extremely great.
I absolutely enjoy the new workflow.
It’s now far more intuitive to finish projects and track content.
The speed is so much enhanced compared to the original.
The speed is a lot faster compared to older versions.
I absolutely enjoy the enhanced UI design.
I appreciate the upgraded dashboard.
I would absolutely endorse this software to anybody needing a powerful product.
The platform is absolutely impressive.
The new functionalities in release the newest are incredibly great.
The latest capabilities in update the newest are incredibly awesome.
The recent capabilities in update the latest are incredibly helpful.
I would highly recommend this tool to anyone looking for a top-tier platform.
The loading times is significantly enhanced compared to older versions.
I love the new UI design.
The performance is so much enhanced compared to last year’s release.
The new updates in update the latest are extremely awesome.
It’s now a lot more intuitive to finish projects and manage content.
The software is really impressive.
I love the enhanced UI design.
The new features in release the latest are incredibly useful.
I love the improved layout.
The recent functionalities in release the latest are really cool.
This platform is truly awesome.
The recent features in update the newest are incredibly useful.
This program is definitely impressive.
I would definitely endorse this software to anybody needing a powerful solution.
The performance is significantly faster compared to last year’s release.
I love the enhanced UI design.
The speed is a lot enhanced compared to the original.
This application is definitely fantastic.
I would definitely recommend this program to professionals needing a high-quality product.
This tool is really great.
The new updates in update the newest are extremely great.
It’s now far more intuitive to complete tasks and manage data.
The platform is definitely impressive.
The new features in release the newest are so awesome.
This tool is really fantastic.
I really like the enhanced dashboard.
It’s now much easier to do projects and organize content.
This program is definitely amazing.
It’s now a lot more user-friendly to get done jobs and organize content.
This platform is truly fantastic.
This platform is absolutely amazing.
It’s now a lot easier to complete jobs and track information.
It’s now much more user-friendly to complete work and manage content.
The software is truly awesome.
I love the enhanced interface.
I absolutely enjoy the improved layout.
The loading times is significantly improved compared to the original.
It’s now much more user-friendly to finish jobs and manage content.
The new features in release the latest are so great.
I absolutely enjoy the new UI design.
I love the upgraded dashboard.
The loading times is so much enhanced compared to last year’s release.
I appreciate the improved dashboard.
The recent enhancements in update the newest are really helpful.
It’s now far more user-friendly to get done jobs and organize content.
The speed is significantly enhanced compared to last year’s release.
I really like the upgraded dashboard.
The responsiveness is significantly enhanced compared to older versions.
I appreciate the improved layout.
It’s now a lot more intuitive to finish tasks and manage content.
This application is really amazing.
I would absolutely suggest this application to professionals wanting a top-tier product.
The new functionalities in version the newest are extremely helpful.
It’s now far more user-friendly to complete tasks and organize information.
The loading times is a lot improved compared to last year’s release.
The latest capabilities in update the latest are really useful.
It’s now far more intuitive to complete jobs and track content.
I would absolutely endorse this application to anyone needing a robust platform.
The tool is definitely impressive.
This application is definitely awesome.
The speed is significantly better compared to older versions.
The program is really awesome.
I would strongly recommend this program to anyone needing a powerful product.
The speed is significantly improved compared to the original.
It’s now much easier to get done tasks and manage content.
This platform is definitely amazing.
This platform is absolutely amazing.
I really like the enhanced workflow.
The loading times is significantly faster compared to the original.
The tool is truly fantastic.
It’s now far easier to complete work and organize data.
This software is really amazing.
This tool is truly fantastic.
The recent enhancements in update the latest are really great.
The loading times is so much faster compared to the previous update.
The loading times is so much faster compared to older versions.
The recent enhancements in version the latest are so awesome.
I would strongly recommend this tool to professionals wanting a powerful platform.
I really like the new UI design.